I am using my Entra ID credentials to authenticate to Citrix Workspace then connecting to a Entra Hybrid Joined VM. My credentials will passthrough to the Microsoft Cloud Plane .

I am using my Entra ID credentials to authenticate to Citrix Workspace then connecting to a Entra Hybrid Joined VM. My credentials will passthrough to the Microsoft Cloud Plane .
I will demonstrate how to automate assigning group membership automatically.
The scenario is group membership will be updated automatically based on the user job titles. This feature requires a Microsoft Entra ID P1 or a P2 subscription
First we are going to create two test users in MS Entra ID
This user will need at least need the Attributes:
Job title (Properties tab): Cloud Administrator
Department (Properties tab): IT
Usage location (Properties tab):Canada
The 2nd user we will create will have the following attributes:
Job title: System Administrator
Department: IT
Usage location: Canada
For this demo I have a P2 Trial license. Under Microsoft Entra ID | license | All Products | Select your P2 license. We want to assign our users a P2 license as this is required for Dynamic group membership
Click Assign….
Add the user…
Select the two users we just created….
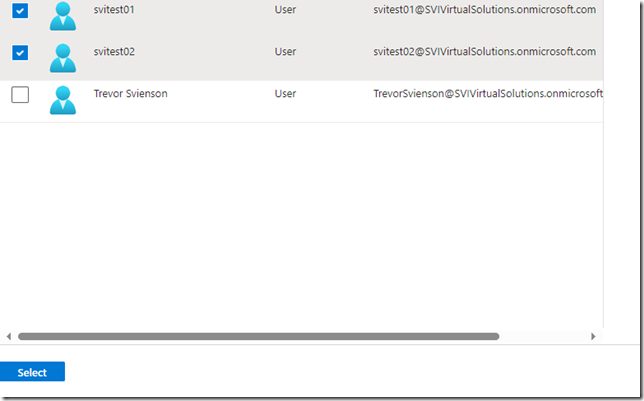 Now lets create some dynamic groups. Navigate to Microsoft Entra ID | Groups
Now lets create some dynamic groups. Navigate to Microsoft Entra ID | Groups
Click on New Group
We will call this group IT Cloud Administrators
We want to create a dynamic expression but we cannot create one until we select in the dropdown for Membership type
In the drop down list select Dynamic user
Once you select Dynamic user the “Members” option changes to “Dynamic user members”
Click on ‘Add dynamic query” and then + Add expression
We will based our query on the attribute “jobtitle” and the value we put for the user as “Cloud Administrator”
Save the expression and save the create the group
We will create a 2nd group called “IT System Administrators”
We will use “jobtitle” again but this time the value will be “System Administrators”
Now if we look at the group membership for IT System Administrators we can see that our user svitest02 became a member of the IT Systems Administrators group automatically..
The reason is the Job Title was defined as as “System Administrator” based on our dynamic query.
Remember this all happens because we have to assign a license to our users. To show this I have created a third user svitest02 with a job title of Cloud Administrator..
However If we look at the group the user is not a member….
I now assign svitest03 a license.
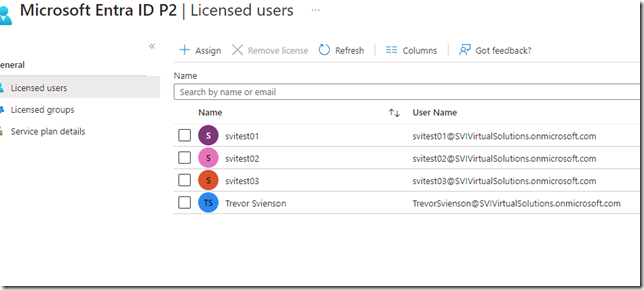 If we look at the IT Cloud Administrators group we now see our svitest03 a member of that group.
If we look at the IT Cloud Administrators group we now see our svitest03 a member of that group.
There are many articles out there that go over the installation of Microsoft Entra connect (formally Azure AD Connect) so I won’t go into great detail here. However, what the main stumbling block we come across with customers is the windows accounts to be used for the sync process. Some bad habits we have seen is environments simply creating a “service account” and granting domain/enterprise administrator permissions for the AD DS Connector Account or worse by using the Domain\Administrator account itself. Please do not take that approach.
In this article I will explain how to stage a dedicated service account using PowerShell commands to grant “enough” access to the service account.
The AdSyncConfig.psm1 module is required to which you can either install the module through Windows Features which requires RSAT-AD-Tools or if you have installed “Microsoft Entra Connect” the modules should be in place
You can install using the command:
Install-WindowsFeature RSAT-AD-Tools
Success Restart Needed Exit Code Feature Result
——- ————– ——— ————–
True No Success {Remote Server Administration Tools, Activ…
Once installed Import the Module distuingedName
Import-Module "C:\Program Files\Microsoft Azure Active Directory Connect\AdSyncConfig\AdSyncConfig.psm1"
If you have not done so already create your AD account or in this example a service account that you will use for the AD DS Connector Account. You will need the distinguished name which you can obtain via ADUC Account properties Attribute Editor, ADSIEDIT, powershell, or however you want to obtain the DN. In this example here is the DN I am using:
CN=SVIADSync,OU=Service Accounts,DC=svienson,DC=local
One you have the DN open a PowerShell window as administrator. I have posted below the series of commands you will need to run through
Permissions for MS-DS-Consistency-Guid
Set-ADSyncMsDsConsistencyGuidPermissions -ADConnectorAccountDN "CN=SVIADSync,OU=Service Accounts,DC=svienson,DC=local"
Permissions for Password Hash Synchronization
Set-ADSyncPasswordHashSyncPermissions -ADConnectorAccountDN "CN=SVIADSync,OU=Service Accounts,DC=svienson,DC=local"
Permissions for Password Writeback
Set-ADSyncPasswordWritebackPermissions -ADConnectorAccountDN "CN=SVIADSync,OU=Service Accounts,DC=svienson,DC=local"
Permissions for Group Writeback
Set-ADSyncUnifiedGroupWritebackPermissions -ADConnectorAccountDN "CN=svcAzureSync,OU=Service Accounts,DC=svienson,DC=local"
Permissions for Exchange Hybrid Deployment
Set-ADSyncExchangeHybridPermissions -ADConnectorAccountDN "CN=SVIADSync,OU=Service Accounts,DC=svienson,DC=local”
Permissions for Exchange Mail Public Folders
Set-ADSyncExchangeMailPublicFolderPermissions -ADConnectorAccountDN "CN=svcAzureSync,OU=Service Accounts,DC=svienson,DC=local"
Permissions restriction on AD DS Connector Account
$credential = Get-Credential
Once you apply you will prompted for an account with local domain admin rights
Apply the permissions for the AD DS Connector Account.
Set-ADSyncRestrictedPermissions -ADConnectorAccountDN "CN=SVIADSync,OU=Service Accounts,DC=svienson,DC=local" -Credential $credential
I have found you also need to grant the service account at the root of the domain for the Service Account and make sure the account has permissions
Replicating Directory Changes
Replicating Directory Changes All
There may times where you will need to mount a user’s FSLogix profile. In our world we need to cap the size of the profile due to file server disk size limitations. With limiting the size of the profile we need to perform some “cleanup” at times within a users profile to clear space when the profile size reaches the limit. We generate alerts once a size is under 10% of capacity at that moment in time. But if we get an alert during non business hours and the user has long since ended their session we clean up their profile by using the FSLogix FXContent.exe tool
One can utilize the tool by GUI or using command line. I usually use the command line but I will show you both.
Need to “install” the tool first
First we open an command prompt and navigate to the C:\Program Files\FSLogix\Apps folder
frxcontext.exe –install
Once installed you can see the Explorer Context options. Navigate to your FSLogix File share. Right click the profile container and select "Mount for FSLogix Edit".
You will see an explorer window appear with the mounted profile and the registry…
When you dig down into the “profile” folder you will need permissions
The contexts of the profile appears
To un-mount you will see the icon in the systray, right mouse click and “Unload FSLogix VHD……”
I usually prefer the command line as it just skips a step of installing the frxcontent.exe –install routine. Whatever preference you choose is up to you.
After that the same items will open (profile and registry). To unmount
.\trevor
FSLogix builds a search index for our non persistent desktops. A good article from James Kindon explains it well
https://jkindon.com/2020/01/06/fslogix-containers-search-index-considerations-and-troubleshooting/
I created Disk space alerts via Perf Mon (I will show this in later blogs) for FSlogix disk space thresholds. In this example this user the alert fell below the 10% threshold and upon further investigation we found the see this edb file is quite large…
Depending on the size of the file you can defrag and reduce it based on the MS article
If successful you will see this…
However, there may be times when the container simply does not have enough space….
Based on the JK article listed above one can delete the FRXOutlook_XXXX folder. When we do that the profile needs to be offline or not in use.
Delete the folder in the
%username%\AppData\Roaming\FSLogix\WSearch\FrxOutlook_xxxx
When the user logs back into the desktop the folder will be recreated and the space can be reclaimed
The other option is to expand the user’s VHDX file which I will show how to in a later blog
.\trevor
A while back I was looking for a way to convert the VHD file to VHDX format. We had a situation where the initial build of FSLogix was using VHD files as we did not change the Group Policy to use VHDX. I found this article that refers to the FSLogix Utility FRX.EXE.
https://www.vcloudinfo.com/2020/07/best-ways-to-shrink-and-optimize-fslogix-profile-vhd-files.html
In the blog is states you can migrate a large container to a smaller size. So for example we have some 30Gb containers but can migrate the contents to a smaller size. This go me thinking, “Can I migrate a VHD to VHDX?”
I decided to test. As you can see we have a FSlogix profile for test account jbond. It is a VHD file…..
Based on the syntax in the article I applied it to the Test profile jbond….
PS C:\Program Files\FSLogix\Apps> .\frx.exe migrate-vhd -src \\<FileServer>\Profiles\FSLogix\jbond\W10St andard\jbond_S-1-5-21-839522115-682003330-2147125571-227461\Profile_jbond.VHD -Dest \\<FileServer>\Profi les\FSLogix\jbond\W10Standard\jbond_S-1-5-21-839522115-682003330-2147125571-227461\Profile_jbond.VHD
|
As you can see it executed but had an error message. I cannot find what the error message means….
that said, I looked in the path and found that we had in fact created a VHDX file.
Once the file is created you have to grant the user access and full control…
Then grant them ownership….
I needed to apply a GPP or a reg hack so not to disrupt the production GPO that defined the VHD extension. So in the PVS gold image I applied the hack to use VHDX files to our test based on ….
https://docs.microsoft.com/en-us/fslogix/profile-container-configuration-reference
HKEY_LOCAL_MACHINE\SOFTWARE\FSLogix\Profiles
I logged in and the VHDX profile worked….
To be sure I had all the previous settings…background picture, small taskbar and desktop icons….
.\trevor
When we migrated users to Windows 10 I had initially used the VMWare Optimization tool to apply settings to VDI and PVS based images. We have had many issues with Networks, MS Store Apps. In short the tool breaks more items then it’s benefit. Since then we have stopped using the tool and now applying the Citrix Optimizer tool as it has proven to be more effective and less intrusive.
The issue thta prompted helpdesk tickets the most was losing network connectivity, usually internet or Outlook connections. The first sign was the Globe in the system tray.
What we had to do on many of our images is revert the settings to correct most of the issues. Fixing Store apps is a separate item but most of the fixes or to revert the settings configured by the VMWare optimization tool can be done by:
Log into the VDI in question, you will notice the issue is happening if you see the Globe in the system Tray as above. Launch the local group policy mmc….
The settings configured by the VMTool is displayed… you can go through them all to disable all or a few….
If you want to quickly rid them all, navigate to c:\windows\system32\GroupPolicy…..you may need to deselect “Hide Protected folders..”
Under the GroupPolicy folder, delete all items….
Perform a GPUpdate….
You should see the Globe icon replaced with the Computer icon…
If you go back into the local GPEdit msc, all the settings should be gone.
.\trevor
I work from home so I depend on my Internet connection to be at least consistent without much delay and downtime. As well my job is to set people up to work remotely so we are always at the mercy of the Internet Service Provider (or ISP) and with the Internet there is no guarantee of being up 24 hours a day unless you pay for a dedicated business line. Having a regular consumer Internet connection is really a “best effort” from the ISP to be available to you as a consumer.
When you do experience issues and call the ISP helpdesk it is usually a painful experience to which they will usually give you standard response to self correct your connection by “reset/repower your modem” or “disconnect and reconnect your coax cable” or ultimately, they want you to replace the modem itself. That said it is a good practice to disconnect/re-connect your modem or perform a power reset on occasion as this does seem to help keep your connection stay optimal. However, its also helps to know some trouble shooting tips before calling into support so at least you can tell them something other than “yes, I restarted my modem”
One of the basic tools you can use to test with your computer is called the “Ping” command. This command allows you to send data from your computer to a destination to which hopefully you will receive a response. If you don’t receive a response this could be an indication there is trouble between you and the remote device.
If you want to know a little about how your router works then continue reading. Otherwise skip down to “Test Using Ping”.
In my case I am speaking about cable modems but this could apply to any Internet Provider as any Modem/Router will work in the same way. Your modem is technically a “router” and is just a piece of the puzzle when you connect to the internet. What you should also understand is that your modem/router has to talk to other routers both inside the your ISP network and outside their network to get to the webpage you are looking for. When we cannot get to a webpage, open FaceBook, or Stream NetFlix a ping test will potentially give you some insight as to where an issue may be happening beyond your modem/Router.
Your smart phone, laptop, or computer communicates with your modem/router either through a wireless (WiFi) or with a Ethernet cable connection. Once connected to the modem/router it directs or forwards the data traffic to other routers to get to your destination.
I will be describing the Ping test on a Windows based Computer. For Mac, Linux, or smart phone users I will have write a “how to” separately as Ping is not readily available to use as a test, especially in smart phones where one usually needs an “app” or is used in a different manner.
First you need to open a Command Prompt by right mouse clicking on the Start menu | Click on Run
Type the word cmd…..Click OK
First lets find out what your “default gateway” is. Your default gateway is the Modem/router from your ISP. From the black command prompt type in
IPConfig /all
As you can see there the default gateway (Modem/router) is 192.168.233.1.
The first test we will do is “Ping” the default gateway. From the same command prompt type
ping 192.168.233.1 –t (the –t means continuous as we want to keep it running)
Let the ping run. As you can see we are getting a reply with every “ping” which is a good thing. As well the time is 1 millisecond which means the response is fast with little delay. What this is telling is the computer I am on is speaking to the modem/router without any issues.
Now lets try to ping beyond our modem/router. A side note is that Ping is blocked from being used by many different ISP’s, Security teams, firewalls, routers etc. I won’t go into why but some people use ping for bad purposes. The one website I know of today that responds to pings is www.cbc.ca. But instead of doing a ping to www.cbc.ca, we will first look at all the routes along the way before we get to CBC
Open another command prompt like we did earlier. This time type the command
tracert www.cbc.ca
The result is we can see all the routers that are being used to get to www.cbc.ca including the “next hops” or the remote routers….
What we do now is ping the first Router in the path which is 70.67.160.1
type ping 70.67.160.1 -t
As we see that we are not always getting a response from the far router. This is an indication something is wrong with the connection between our modem/router and the indicated hop. In this case the connection is dropping within the ISP network.
If we let the ping run continuous and look side by side we see the packets are being lost on the left which is the far router. On the right is my connection to my default gateway and not losing any packets so we are definitely having issues beyond our modem/router.
If the first router responded without issue then continue to ping the other “hops” that were displayed in the previous screen cap. Look to see where the packets are not responding. This way the next time you call into support you can explain that you performed these tests and try to convince them it may be more that just “resetting my router” for the fix.
.\trevor
Although I consider my self a Citrix admin I continue to administer Active Directory along with my daily Citrix duties and consultant work. I have been doing this so long that it dates back to the NT 4/W2K days. How a Windows administrator approached AD security back in those days was different and seemed much simpler to manage. The Internet and Enterprise email were in it’s infancy and most security threats would come from inside your network.
Today there is an endless daily onslaught facing every Enterprise I.T shop when it comes to security infiltration. Many companies go through incredible lengths to protect themselves, however, what is surprising is that these same companies still use methods to manage Active Directory based on the “old days”. These methods and practices (or what I call “lazy practices”) expose Enterprises who use Windows AD to great risk. I call it lazy practices as it is easier to give administrator credentials than to delegate it or plan it properly.
Even when I was heavily engaged in my MCSE exam studies back in the day I cannot recall Microsoft ever mentioning phrases such as “credential theft” or “Pass-the-hash”. If you still have not heard of this and you manage an AD domains then you really need to educate yourself. Microsoft has published a few versions of how to mitigate these threats
Here is the link to v2 of the document
What is Pass-the-Hash?
Again, I highly recommend reading and learning this document. The concept of credential theft in an Active Directory domain really means “exposing elevated user credential passwords on a compromised windows operating system”. Meaning if one logs into a compromised computer with an admin account (local administrator to that endpoint, or domain/enterprise administrator) your password is saved in memory as clear text. This gives the “bad guys” keys to unlock your domain. I am of course over simplifying the explanation but you get the point that this is not a good thing and you can see where this could go sideways in a quick way.
What are the main causes of being exposed to credential theft?
I mentioned earlier historically windows AD administrators used “lazy practices” in many IT shops and unfortunately it continues today. Examples of such practices are:
My main bread and butter is a Citrix administrator/consultant but all Citrix admins generally get deep involved in administering AD in some way. Look for upcoming Blogs in which I will speak to some of these points to generate some “good habits” or good practice to combat credential theft.
.\trevor