There are many articles out there that go over the installation of Microsoft Entra connect (formally Azure AD Connect) so I won’t go into great detail here. However, what the main stumbling block we come across with customers is the windows accounts to be used for the sync process. Some bad habits we have seen is environments simply creating a “service account” and granting domain/enterprise administrator permissions for the AD DS Connector Account or worse by using the Domain\Administrator account itself. Please do not take that approach.
In this article I will explain how to stage a dedicated service account using PowerShell commands to grant “enough” access to the service account.
Power Shell Module AdSyncConfig.psm1
The AdSyncConfig.psm1 module is required to which you can either install the module through Windows Features which requires RSAT-AD-Tools or if you have installed “Microsoft Entra Connect” the modules should be in place
You can install using the command:
Install-WindowsFeature RSAT-AD-Tools
Success Restart Needed Exit Code Feature Result
——- ————– ——— ————–
True No Success {Remote Server Administration Tools, Activ…
Once installed Import the Module distuingedName
Import-Module "C:\Program Files\Microsoft Azure Active Directory Connect\AdSyncConfig\AdSyncConfig.psm1"
Granting Permissions to Service Account
If you have not done so already create your AD account or in this example a service account that you will use for the AD DS Connector Account. You will need the distinguished name which you can obtain via ADUC Account properties Attribute Editor, ADSIEDIT, powershell, or however you want to obtain the DN. In this example here is the DN I am using:
CN=SVIADSync,OU=Service Accounts,DC=svienson,DC=local
One you have the DN open a PowerShell window as administrator. I have posted below the series of commands you will need to run through
Permissions for MS-DS-Consistency-Guid
Set-ADSyncMsDsConsistencyGuidPermissions -ADConnectorAccountDN "CN=SVIADSync,OU=Service Accounts,DC=svienson,DC=local"
Permissions for Password Hash Synchronization
Set-ADSyncPasswordHashSyncPermissions -ADConnectorAccountDN "CN=SVIADSync,OU=Service Accounts,DC=svienson,DC=local"
Permissions for Password Writeback
Set-ADSyncPasswordWritebackPermissions -ADConnectorAccountDN "CN=SVIADSync,OU=Service Accounts,DC=svienson,DC=local"
Permissions for Group Writeback
Set-ADSyncUnifiedGroupWritebackPermissions -ADConnectorAccountDN "CN=svcAzureSync,OU=Service Accounts,DC=svienson,DC=local"
Permissions for Exchange Hybrid Deployment
Set-ADSyncExchangeHybridPermissions -ADConnectorAccountDN "CN=SVIADSync,OU=Service Accounts,DC=svienson,DC=local”
Permissions for Exchange Mail Public Folders
Set-ADSyncExchangeMailPublicFolderPermissions -ADConnectorAccountDN "CN=svcAzureSync,OU=Service Accounts,DC=svienson,DC=local"
Permissions restriction on AD DS Connector Account
$credential = Get-Credential
Once you apply you will prompted for an account with local domain admin rights
Apply the permissions for the AD DS Connector Account.
Set-ADSyncRestrictedPermissions -ADConnectorAccountDN "CN=SVIADSync,OU=Service Accounts,DC=svienson,DC=local" -Credential $credential
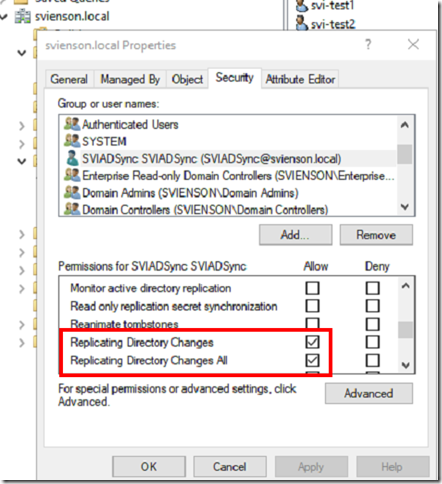
One Additional Permission
I have found you also need to grant the service account at the root of the domain for the Service Account and make sure the account has permissions
Replicating Directory Changes
Replicating Directory Changes All