Although I consider my self a Citrix admin I continue to administer Active Directory along with my daily Citrix duties and consultant work. I have been doing this so long that it dates back to the NT 4/W2K days. How a Windows administrator approached AD security back in those days was different and seemed much simpler to manage. The Internet and Enterprise email were in it’s infancy and most security threats would come from inside your network.
Today there is an endless daily onslaught facing every Enterprise I.T shop when it comes to security infiltration. Many companies go through incredible lengths to protect themselves, however, what is surprising is that these same companies still use methods to manage Active Directory based on the “old days”. These methods and practices (or what I call “lazy practices”) expose Enterprises who use Windows AD to great risk. I call it lazy practices as it is easier to give administrator credentials than to delegate it or plan it properly.
Even when I was heavily engaged in my MCSE exam studies back in the day I cannot recall Microsoft ever mentioning phrases such as “credential theft” or “Pass-the-hash”. If you still have not heard of this and you manage an AD domains then you really need to educate yourself. Microsoft has published a few versions of how to mitigate these threats
Here is the link to v2 of the document
What is Pass-the-Hash?
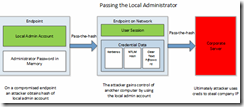
Again, I highly recommend reading and learning this document. The concept of credential theft in an Active Directory domain really means “exposing elevated user credential passwords on a compromised windows operating system”. Meaning if one logs into a compromised computer with an admin account (local administrator to that endpoint, or domain/enterprise administrator) your password is saved in memory as clear text. This gives the “bad guys” keys to unlock your domain. I am of course over simplifying the explanation but you get the point that this is not a good thing and you can see where this could go sideways in a quick way.
What are the main causes of being exposed to credential theft?
I mentioned earlier historically windows AD administrators used “lazy practices” in many IT shops and unfortunately it continues today. Examples of such practices are:
- Misuse of privileged accounts is the primary concern (using domain admin as a daily account)
- Administrator Accounts are often over-allocated
- Over use of local administrative rights on endpoints
- Non standard endpoints and procedures
- Not using AD delegation rights to it’s full potential
My main bread and butter is a Citrix administrator/consultant but all Citrix admins generally get deep involved in administering AD in some way. Look for upcoming Blogs in which I will speak to some of these points to generate some “good habits” or good practice to combat credential theft.
.\trevor