To ensure our XenDesktops are up and functional for the day I have created a morning check script perform this task. The check will look for:
- UNREGISTERED MACHINES
- REGISTERED MACHINES
- MACHINES IN MAINTENANCE MODE
Ideally we will only see machines that in the REGISTERED category. Here is the PowerShell script that was created and run from the Desktop Delivery Controller
Reference
XenDesktop Monitoring: Desktop Availability
http://blogs.citrix.com/2012/10/27/xendesktop-monitoring-desktop-availability/
|
# # Set-ExecutionPolicy RemoteSigned # Asnp Citrix.* # $badVMs = Get-BrokerDesktop -PowerActionPending $false -PowerState On -SummaryState Available -WillShutdownAfterUse $true -MaxRecordCount 5000 # $recipients = "alert.citrix@svi-virtualsolutions.com" [string]$unregisteredVMs = (Get-BrokerDesktop -MaxRecordCount 5000 | ? {($_.RegistrationState -eq ‘Unregistered’) -and ($_.PowerState -eq ‘On’)} | select HostedMachineName,DesktopGroupName,LastDeregistrationReason | ft -wrap -autosize | Out-String) [string]$registeredVMs = (Get-BrokerDesktop -MaxRecordCount 5000 | ? {($_.RegistrationState -eq ‘Registered’) -and ($_.PowerState -eq ‘On’)} | select HostedMachineName,DesktopGroupName,LastDeregistrationReason | ft -wrap -autosize | Out-String) [string]$maintenanceModeVMs = (Get-BrokerDesktop -MaxRecordCount 5000 | ? {$_.InMaintenanceMode -eq ‘True’} | select HostedMachineName,DesktopGroupName,LastDeregistrationReason | ft -wrap -autosize | Out-String) [string]$emailBody = "UNREGISTERED MACHINES `n`n`n $unregisteredVMs" + "REGISTERED MACHINES `n $registeredVMs" + "`n" + "MACHINES IN MAINTENANCE MODE `n $maintenanceModeVMs" # send-mailmessage -from $fromEmail -to $recipients -subject "XenDesktop Prod Daily Check $currentTime" -body $emailBody |
Here is the end result via email:
|
UNREGISTERED MACHINES |
The script calls CheckForVMsInMTCMode.ps1 is located on the DDC in C:\tools folder. The script is run as a scheduled task which launches at 7 am daily.
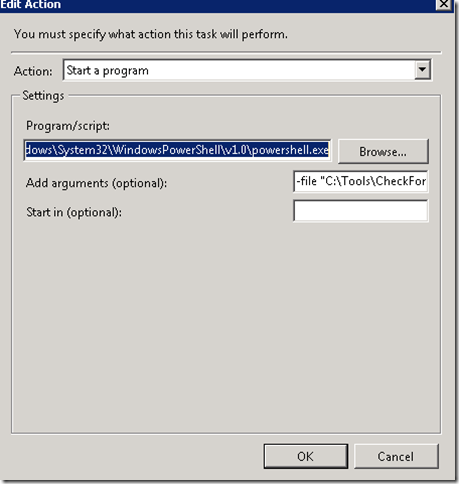
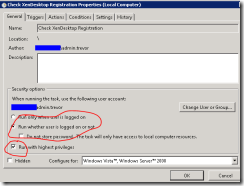
Here is how the task is configured on the DDC:
Inside the daily task this is the Action. Simply launches PowerShell and then a command argument for launching the file:
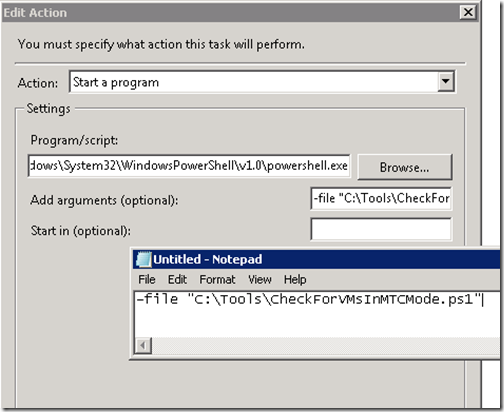
Here is a more closer look at the argument:
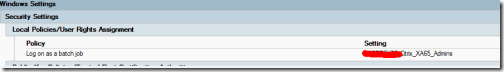
Also remember to add the "rights" to run the file.
Testing the Script
In order to get this to work I ran some tests to see if this would work. A good references to do this is
Weekend Scripter: Use the Windows Task Scheduler to Run a Windows PowerShell Script
http://blogs.technet.com/b/heyscriptingguy/archive/2012/08/11/weekend-scripter-use-the-windows-task-scheduler-to-run-a-windows-powershell-script.aspx
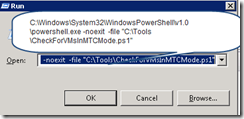
From the DDC I opened a run command and typed this
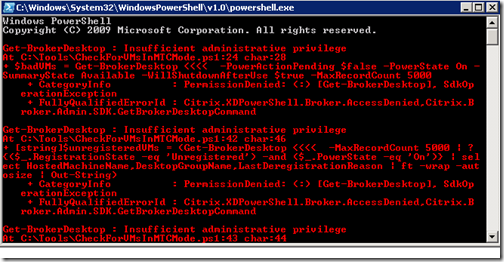
As you can see from the screen cap above I was receiving an "Insufficient administrative privilege" message which simply meant I did not have enough privileges to run the XenDesktop cmdlet. I had to elevate my privileges in order for this to complete from the run command. I also had to do the same in the daily task:
Another reference to run PowerShell from a daily task.
Run PowerShell Scripts from Task Scheduler
http://community.spiceworks.com/how_to/show/17736-run-powershell-scripts-from-task-scheduler