Monthly Archives: March 2014
Debugging XenApp Crash Errors
We have been getting reports of more and more IE and Outlook crashes. So to try and get a little more insight into this I am invoking the application crash dumps to try to see the issue. This is not limited to Citrix servers but can be done via Windows 7 or 2008 so if you are having issues with application crashes this may help you find the problem. Here is how I did this:
Enable Crash dumps on XenApp
Based on this article http://support.citrix.com/article/CTX118614 I created a GPO preference to enable this feature. Here is the configurations:
As you can see once I did GPUPDATE I started to see some .dmp files.
Install Debugging Tools
Then one needs to install the debugging tools. This can be found at http://msdn.microsoft.com/en-us/windows/hardware/hh852365 and the link within that page is http://www.microsoft.com/en-us/download/confirmation.aspx?id=8279 (Debugging Tools for Windows (WinDbg)
Executing the WindDebug command
Once you have the tools installed you navigate to the tools folder "c:\Program Files\Debugging Tools for Windows (x64)>cd "c:\Program Files\Debugging Tools for Windows (x64)".
The command to execute the tools is
c:\Program Files\Debugging Tools for Windows (x64)>windbg -y srv*c:\symbols*http://msdl.microsoft.com/download/symbols -i c:\windows\i386 -z <path to dump files>
The path in red indicates that I simply used the Microsoft provided symbols online. The green I simply mapped a drive to the location of the files. In this case it is the D drive on the XenApp server. So my command looks like:
c:\Program Files\Debugging Tools for Windows (x64)>windbg -y srv*c:\symbols*http://msdl.microsoft.com/download/symbols -i c:\windows\i386 –z D:\Citrix\Crashdumps\iexplore.exe.22840.dmp
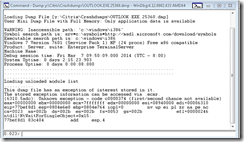
Once the command is executed the debug screen will appear like below:
Analyzing the Crash Dump
Once the Windebugging tool executes you want to peform a more verbose output. This is done by simply entering in !analyze -v on the bottom line
The reason I created the preferences is that my XenApp servers are provisioned and read-only. As well that I will disable the preferences when I am done troubleshooting. I have a D: drive that I use which is local physical hardware to capture the dumps which also is where my vDiskCache, page file, etc live.
As you can see once I did GPUPDATE I started to see some .dmp files.
|
Microsoft (R) Windows Debugger Version 6.12.0002.633 AMD64 Loading Dump File [y:\Citrix\Crashdumps\OUTLOOK.EXE.25360.dmp] WARNING: Inaccessible path: ‘c:\windows\i386’ *** ERROR: Symbol file could not be found. Defaulted to export symbols for rsintcor32.dll – FAULTING_IP: EXCEPTION_RECORD: ffffffff — (.exr 0xffffffffffffffff) PROCESS_NAME: OUTLOOK.EXE ERROR_CODE: (NTSTATUS) 0xc0000374 – A heap has been corrupted. EXCEPTION_CODE: (NTSTATUS) 0xc0000374 – A heap has been corrupted. EXCEPTION_PARAMETER1: 77cd4270 MOD_LIST: <ANALYSIS/> NTGLOBALFLAG: 0 APPLICATION_VERIFIER_FLAGS: 0 FAULTING_THREAD: 00005adc BUGCHECK_STR: APPLICATION_FAULT_ACTIONABLE_HEAP_CORRUPTION_heap_failure_block_not_busy_DOUBLE_FREE PRIMARY_PROBLEM_CLASS: ACTIONABLE_HEAP_CORRUPTION_heap_failure_block_not_busy DEFAULT_BUCKET_ID: ACTIONABLE_HEAP_CORRUPTION_heap_failure_block_not_busy LAST_CONTROL_TRANSFER: from 77c9f659 to 77c9e753 STACK_TEXT: FOLLOWUP_IP: SYMBOL_STACK_INDEX: 6 SYMBOL_NAME: msvcr90!realloc+35f FOLLOWUP_NAME: MachineOwner MODULE_NAME: msvcr90 IMAGE_NAME: msvcr90.dll DEBUG_FLR_IMAGE_TIMESTAMP: 4ca2ef57 STACK_COMMAND: ~23s; .ecxr ; kb FAILURE_BUCKET_ID: ACTIONABLE_HEAP_CORRUPTION_heap_failure_block_not_busy_c0000374_msvcr90.dll!realloc BUCKET_ID: APPLICATION_FAULT_ACTIONABLE_HEAP_CORRUPTION_heap_failure_block_not_busy_DOUBLE_FREE_msvcr90!realloc+35f WATSON_STAGEONE_URL: Followup: MachineOwner |