I was recently tasked with testing a two factor authentication product called Symantec’s Validation and ID Protection service with NetScaler. I won’t go into too much detail of Symantec VIP but you can get a good insight by viewing Symantec’s site on the product http://www.symantec.com/products/videos.jsp?pcid=pcat_security&pvid=vip_1
What I will mention is that the product is similar to the RSA two factor method to which you will need a token ID number to authenticate with but without the pain of carrying around a token ID generator. The Symantec’s product does have a token ID needed to authenticate but it is software based so you can install the token ID generator onto your iPad, Blackberry, or personal computer. So in the end you eliminate the method of carrying a separate device that generates a token ID. I’ll show you what the application for VIP looks like a little later.
Items needed:
- Windows based server for the VIP application back end software
- NetScaler/Access Gateway
I will not show how to setup the Symantec VIP Server but rather focus on the NetScaler setup. I am writing this based on a scenario that the company security team has approached you (you being the NetScaler/Citrix administrator) to configure two factor authentication on your NetScaler using the only information from the security guys which is the IP address of the VIP server and a shared secret.
Preliminary Information
The Symantec documentation only assumes one will use Web Interface or Windows based computers and not mobile devices such as iPad or Android devices. So I have gathered the necessary resources needed to configure the mobile devices that use the Citrix Receiver (or non Windows) for our Symantec VIP test.
- How to Configure Dual Authentication on Access Gateway Enterprise Edition for Use with iPhone and iPad
http://support.citrix.com/article/CTX125364 - How to Customize the Logon Page of an Access Gateway Enterprise Edition Release 9.2 Appliance
http://support.citrix.com/article/CTX126206
Just as an FYI Symantec’s Documentation shows the following as the configuration order.
- Install and Configure VIP Enterprise Gateway
- Configure the Citrix NetScaler Device with VIP Enterprise Gateway
- Authenticate Users via the Access Gateway or Client
NetScaler Configuration – Adding the RADIUS Authentication Server
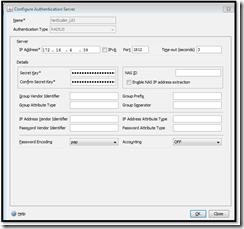
I am going to assume that you already have SmartAccess configured and working in your environment which means you already have a working NetScaler with a SSL cert and XenApp/XenDesktop in play. First we need to add a secondary authentication server. In my case a second server is called NetScaler_UO
- From the Servers tab, click Add.
- In the Create Authentication Server dialog box, type a name for the server in the Name field (for example, "NetScaler_UO"
- Select RADIUS as the Authentication Type, and in the Server section, specify values for each parameter:
- IP Address: Enter the IP Address of the Validation Server or Symantec VIP server
- Port: Enter the port number of the Validation Server (by default is 1812)
- Time-out: Enter a value in seconds (leave default)
The results looks like this:
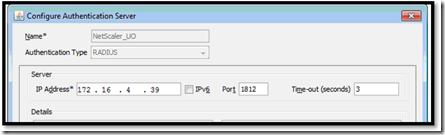
4. Under the Details section, enter the RADIUS Shared Secret Key and confirm it. Remember this is the shared key given to you by the security guys.
Add the RADIUS Authentication Policy
For these steps we will refer to the Citrix article http://support.citrix.com/article/CTX125364. Remember that the Symantec guides assume everyone will use a Windows PC to connect. The Citrix article allows the Citrix mobile receiver to work with mobile devices as well.
Configuring Access Gateway Enterprise Edition for Two Factor Authentication with iPad and iPhone:
5. In the Access Gateway Configuration Utility, go to Access Gateway > Policies > Authentication and create an authentication policy for LDAP and RSA for mobile devices and non-mobile devices. This is necessary to avoid a logic condition that could allow users to bypass the RADIUS Authentication.
6. Create an LDAP policy for the Mobile Devices. To bind this policy to only mobile devices, use the following expression: REQ.HTTP.HEADER User-Agent CONTAINS CitrixReceiver:
7. Create a RADIUS policy for the Mobile Devices. To bind this policy to only mobile devices, use the expression below: REQ.HTTP.HEADER User-Agent CONTAINS CitrixReceiver:
8. Create an LDAP policy for non-mobile devices. To bind this policy to only non-mobile devices, use the expression that follows: REQ.HTTP.HEADER User-Agent NOTCONTAINS CitrixReceiver:
9. Create a Radius policy for non-mobile devices. To bind this policy to only non-mobile devices, use the following expression: REQ.HTTP.HEADER User-Agent NOTCONTAINS CitrixReceiver:
10. Go to the properties of the Access Gateway Virtual Server and go to the Authentication tab. On the Primary Authentication Policies, add the vip_mobile policy as top priority and the ldap_nonmobile policy as secondary priority:
11. On the Secondary Authentication Policies, add the ldap_mobile Policy as top priority, followed by the vip_nonmobile Policy.
Customize the Web Interface Logon
Now that everything is configured you should notice that NetScaler login will have three form field but the the labels are not user friendly as the default after our configuration is username, password 1, and password 2. In our case we are using a username, password, and a Token ID to login. One can customize the fields based on this article http://support.citrix.com/article/CTX126206 so the end result looks like this:
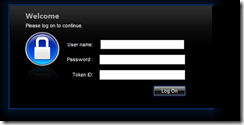
The Symantec VIP software
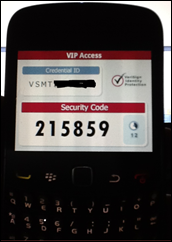
The final piece to this puzzle is using a Token ID to login. (Well that is not entirely true as your security guys would of setup a Symantec/VeriSign login site to register your AD credentials to associate to a profile, but I’ll let the Symantec and security guys explain that one). One can install the VIP software on your iPad, Windows PC, or Blackberry. In my case I carry a Blackberry so I decided to install the VIP software on my BB and use this as my Token ID generator since I carry it everywhere I go.
In the screen cap below you will notice a number beginning with VSMT that will need to be registered. Here is the iPad version found in the App Store:
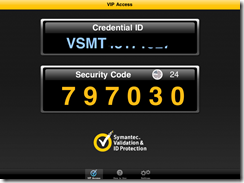
BlackBerry version found in BB World:
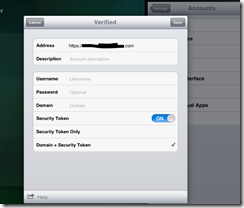
If you are using an IOS device such as an iPad you need to select the Security Token and Domain when creating your account:
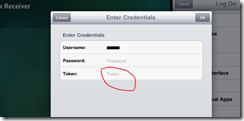
When authenticating to your Web Interface you need to enter in the Symantec VIP token ID:
So far I find it very easy to work with regards to authenticating. We have been testing Symantec VIP FOR the better part of two months and it has worked like clockwork. We will see once it is introduced to the masses how easy it will be to manage and maintain users on a regular basis.
>trevor